Supreme Tips About How To Detect Man In The Middle Attack

With the advent and rising popularity of.
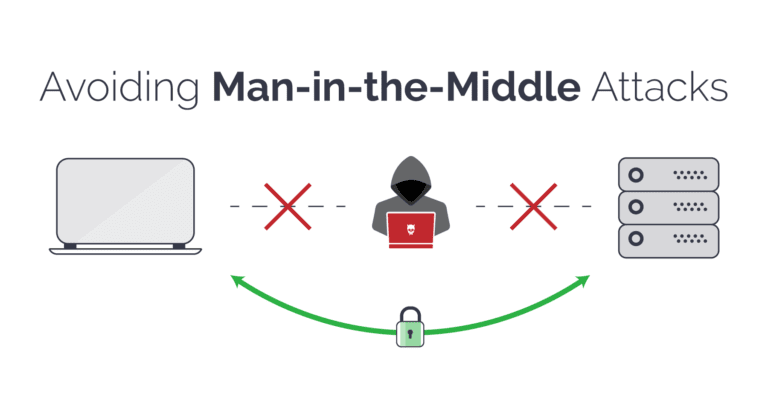
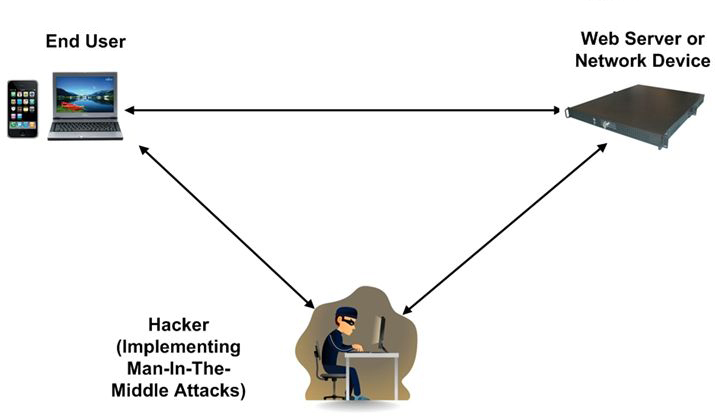
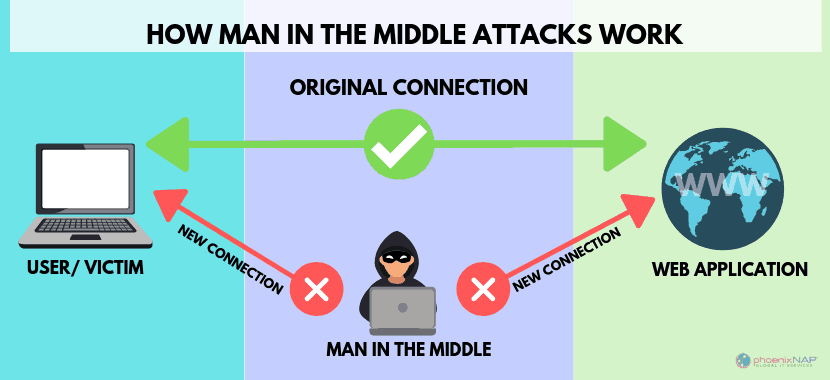
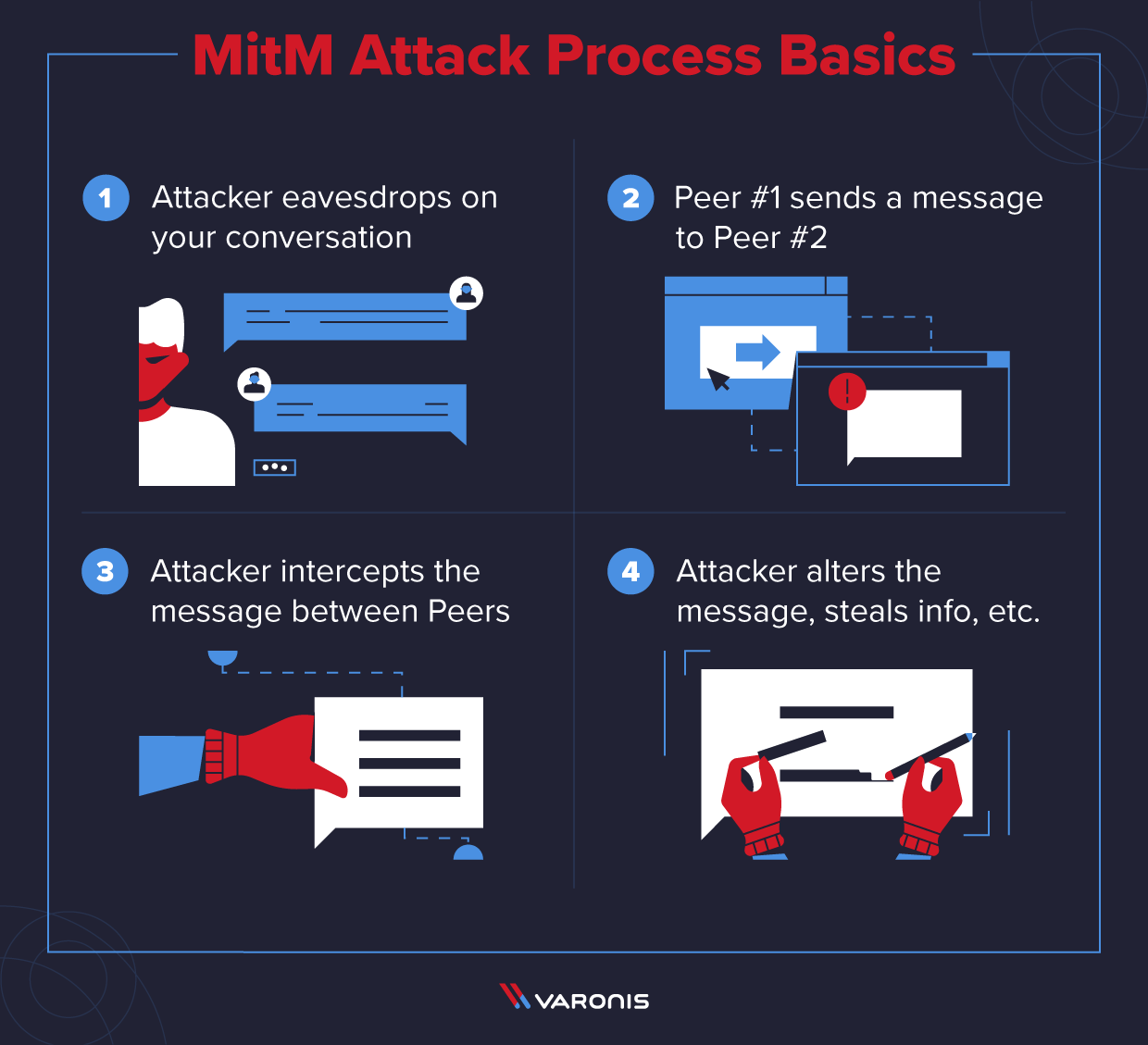
How to detect man in the middle attack. After all, the whole point is to allow the attacker to bypass security. Share improve this answer answered. However, there are a few signs which indicate a mitm attack when browsing.
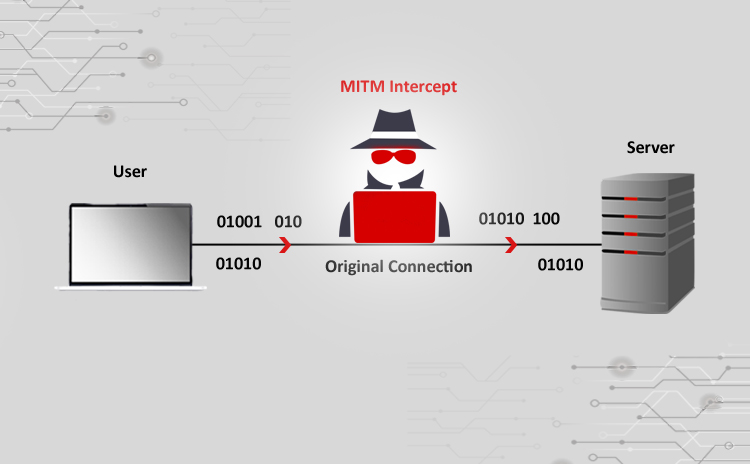
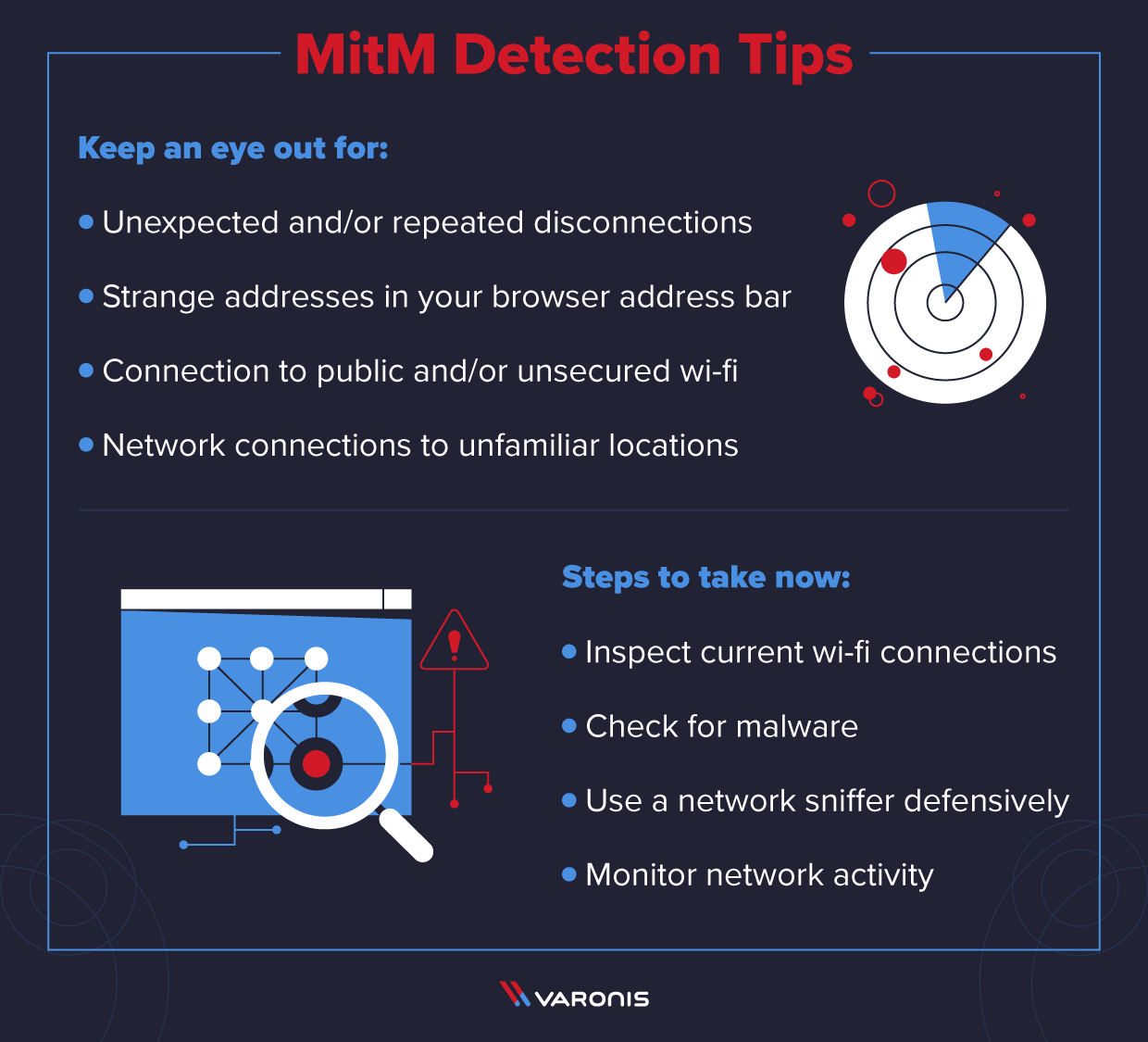
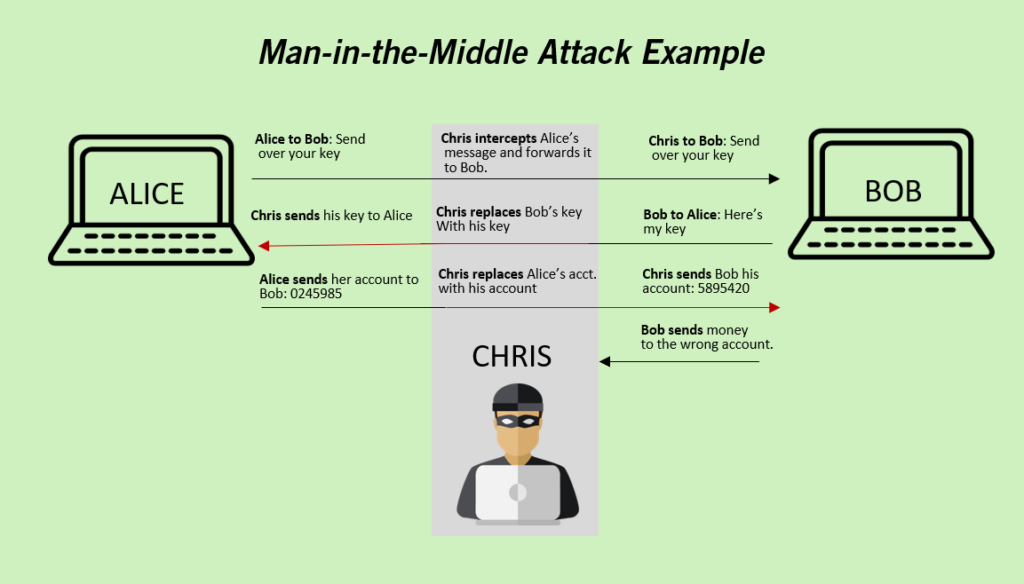
Analyze connection records to look out for repeated disconnections. Have you ever wondered if someone is trying to spoof your network to acquire confidential information? The name of this attack encapsulates the main principle of its execution:
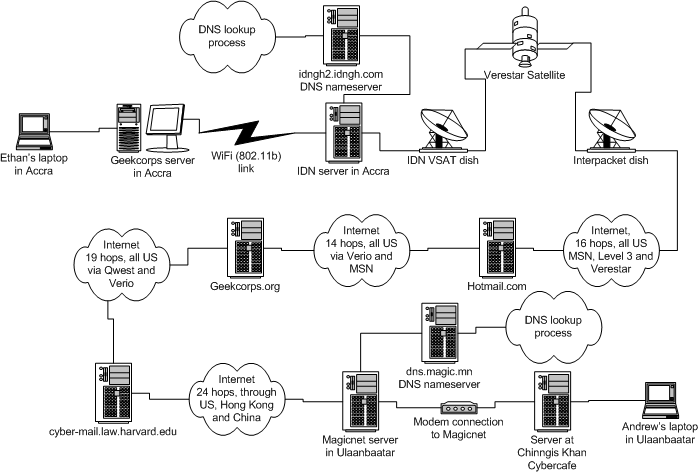
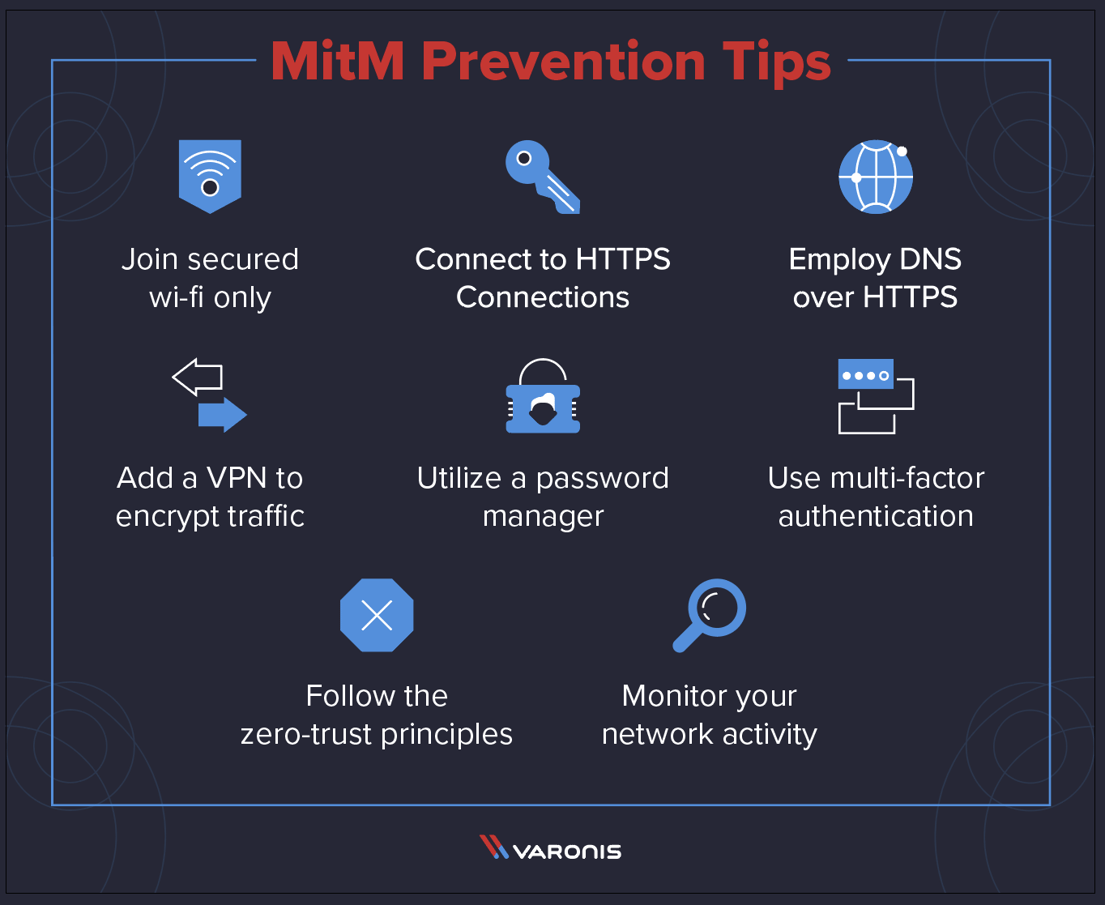
To detect potential attacks, parties check for discrepancies in response times. Update default usernames and passwords on your routers and all connected devices to strong, unique passwords. In the output shown, the usbank.com and whitehouse.gov sites are the only ones not being decrypted.
Here are the steps to detect, disable and enable smbv1 client and server by using powershell commands. If you or any of your employees. What causes a man in the middle attack on windows;
A new heuristic virus which dosn't being detected in past but. If the router mac address is the same as any other node (device) then that devise is the man in the middle. Scan your website and network for malware.
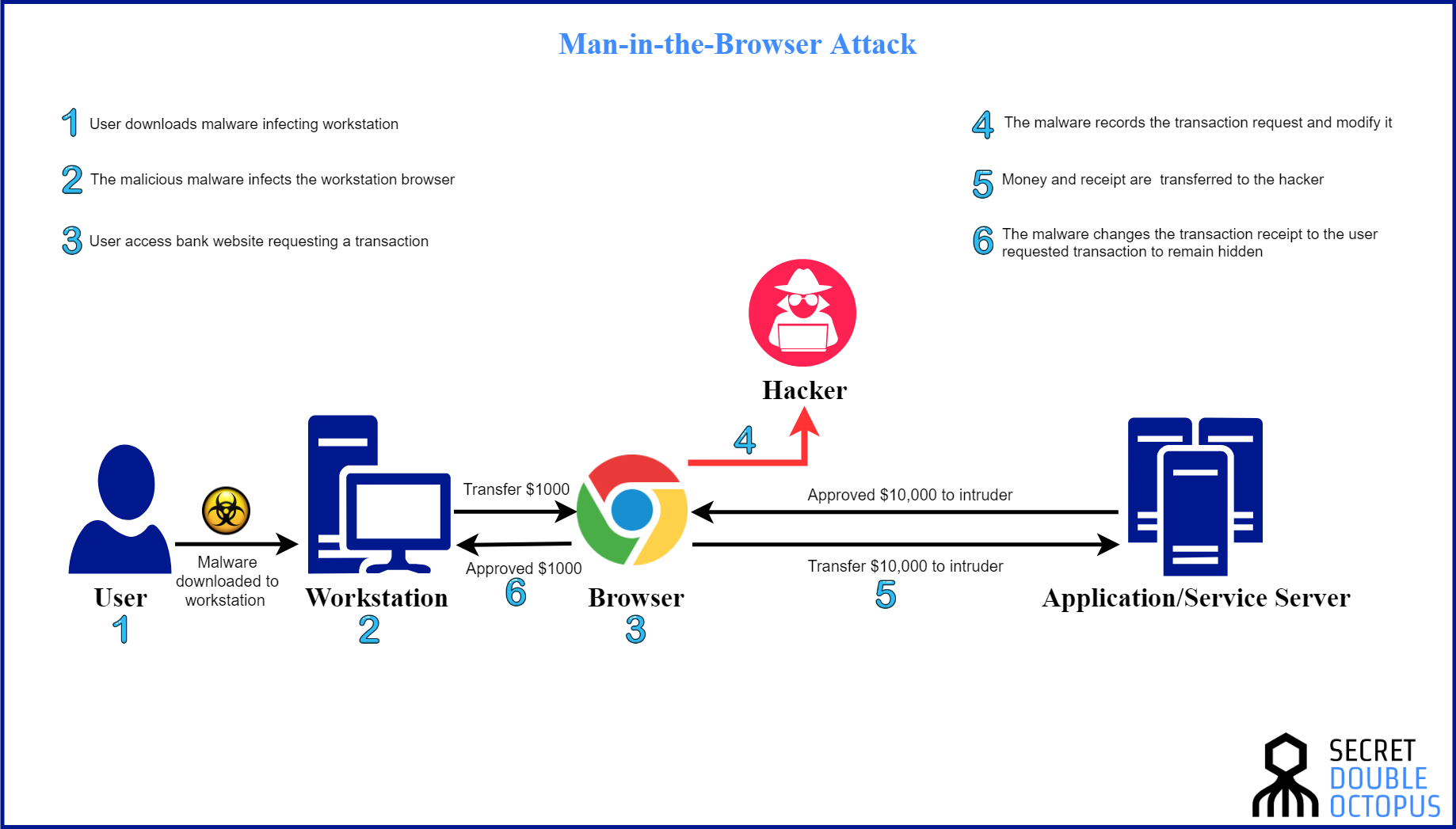
Man in the middle attack tools. Threat actors insert a malicious software or device between the victim's.