Fine Beautiful Tips About How To Protect Des Against Exhaustive Key Search

Joe kilian and phillip rogaway.
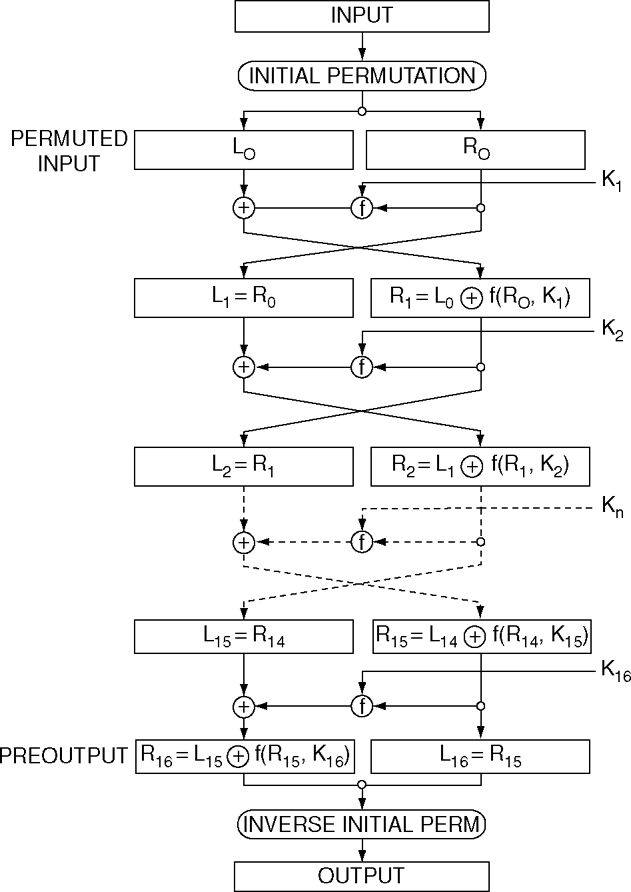
How to protect des against exhaustive key search. This construction was first suggested by ron rivest as a computationally. This construction was first suggested by rivest as a. This paper proves, in a formal model, that the.
How to protect des against exhaustive key search (an analysis of desx). This construction was first suggested by ron rivest as a. This paper proves, in a formal model, that the desx.
This construction was first suggested by ron rivest as a. This construction was first suggested by rivest as a. This paper proves, in a formal model, that the desx.
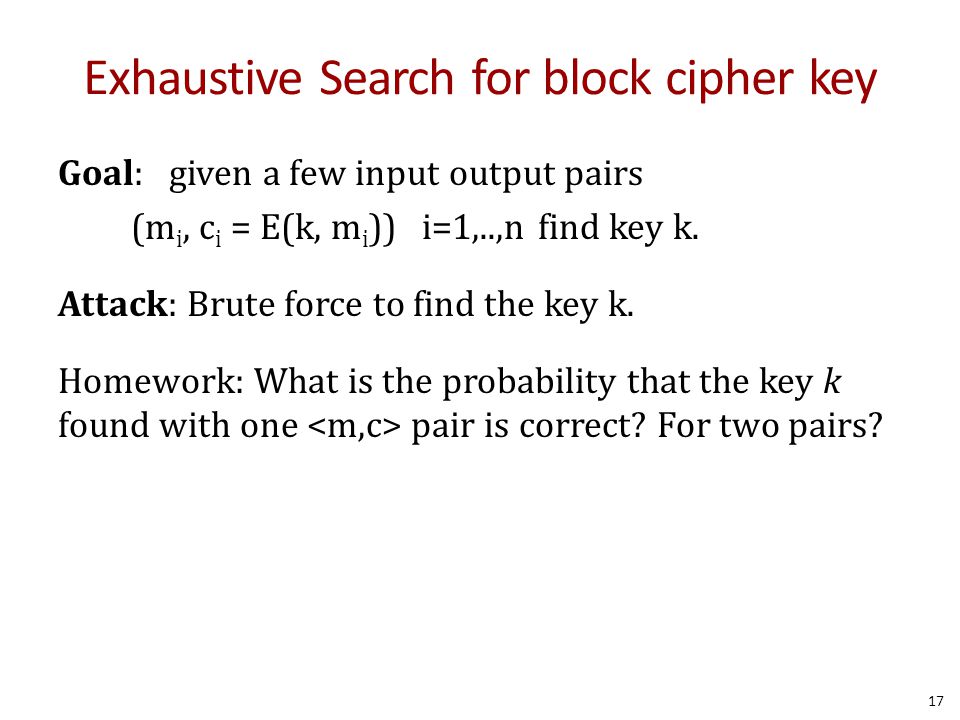
There have been many approaches suggested for reducing des’s vulnerability to exhaustive key search.



![Average Time Required For Exhaustive Key Search [20] | Download Table](https://www.researchgate.net/profile/Joseph-Panford/publication/306011867/figure/tbl2/AS:667697696227335@1536202944456/Average-Time-Required-for-Exhaustive-Key-Search-20_Q320.jpg)






![Average Time Required For Exhaustive Key Search [20] | Download Table](https://www.researchgate.net/publication/306011867/figure/tbl2/AS:667697696227335@1536202944456/Average-Time-Required-for-Exhaustive-Key-Search-20.png)
![Average Time Required For Exhaustive Key Search [20] | Download Table](https://www.researchgate.net/profile/Joseph-Panford/publication/306011867/figure/tbl2/AS:667697696227335@1536202944456/Average-Time-Required-for-Exhaustive-Key-Search-20_Q640.jpg)



